As development continues to advance at a quick speed, stresses over how our information is being assembled, shared, and used have become logically normal. From virtual amusement stages to sharp home contraptions, our web-based practices are ceaselessly being noticed, raising issues about how we can shield our security in this interconnected world.
With the creating inescapability of data breaks and online assurance humiliations, it has become basic for individuals to take proactive Technological Advancements on Privacy measures to safeguard their own information. From using encoded illuminating applications to regularly invigorating insurance settings through web-based diversion accounts, there are various advances that can be made to restrict the risks of computerized risks.
Measures to Protect Privacy Amid Rapid Technological Advancements
In the current fast-moving world, it seems like reliably brings new mechanical types of progress that simplify our lives and are more accommodating. Nevertheless, with these technological advancements furthermore come stresses over security and the protection of individual information.
As we continuously rely upon advancement for correspondence, money-related trades, and in any event, prosperity checking, it is basic to take the necessary steps to safeguard our security in the mechanized age.
Strengthening Data Protection Laws
One of the primary measures to protect privacy amid rapid technological advancements is to ensure that there are strong data affirmation guidelines set up. These guidelines should manage how associations accumulate, store, and use individual data, and should integrate courses of action for straightforwardness, consent, and the choice to be dismissed. By taking into account associations answerable for how they handle our own information, we can help with hindering data breaks and misrepresentation.
Encryption and Secure Communication
Another technique for defending assurance in old age is to use encryption and secure specific gadgets at whatever point what is happening permits. Encryption scrambles data so it should be scrutinized by supported parties, making it altogether more moving for developers to hinder and get to sensitive information. By including encryption for messages, illuminating applications, and online trades, we can help ensure that our own data stays private and secure.
Executing Two-Factor Confirmation
Two-factor approval is one more huge measure that can help with protect privacy amid rapid technological advancements. By anticipating that clients should give two kinds of affirmation, preceding getting to a record or organization, two-factor approval adds an extra layer of security that can help with hindering unapproved access. This fundamental yet effective measure can go very far toward protecting our own information on the web.
Monitoring Privacy Settings
In the present interconnected world, an extensive part of us have accounts on various virtual diversion stages, applications, and destinations. It is influential to know about security settings and to regularly review and update them to ensure that we are simply sharing the information we want to share. By changing security settings to limit who can see our posts, photos, and individual nuances, we can lessen our web-based impression and defend our insurance from nosy eyes.
Educate Yourself As well as other People
Finally, conceivably the best measure we can take to protect privacy amid rapid technological advancements is to show ourselves as well as others about the risks and best practices for online security. By staying informed about the latest risks and security endeavours, we can make extra-taught decisions about how we use development and defend our own information. It is similarly fundamental to teach buddies, family, and partners about the meaning of safety and the means they can take to guard their own data.
Moves toward using Gauth for Queries Solution
Gauth is an integral asset that can be utilized to take care of a large number of issues rapidly and productively. Whether you really want assistance with math, science, or some other subject, Gauth is here to help you. In this part, we will examine the moves toward the use of Gauth for critical thinking.
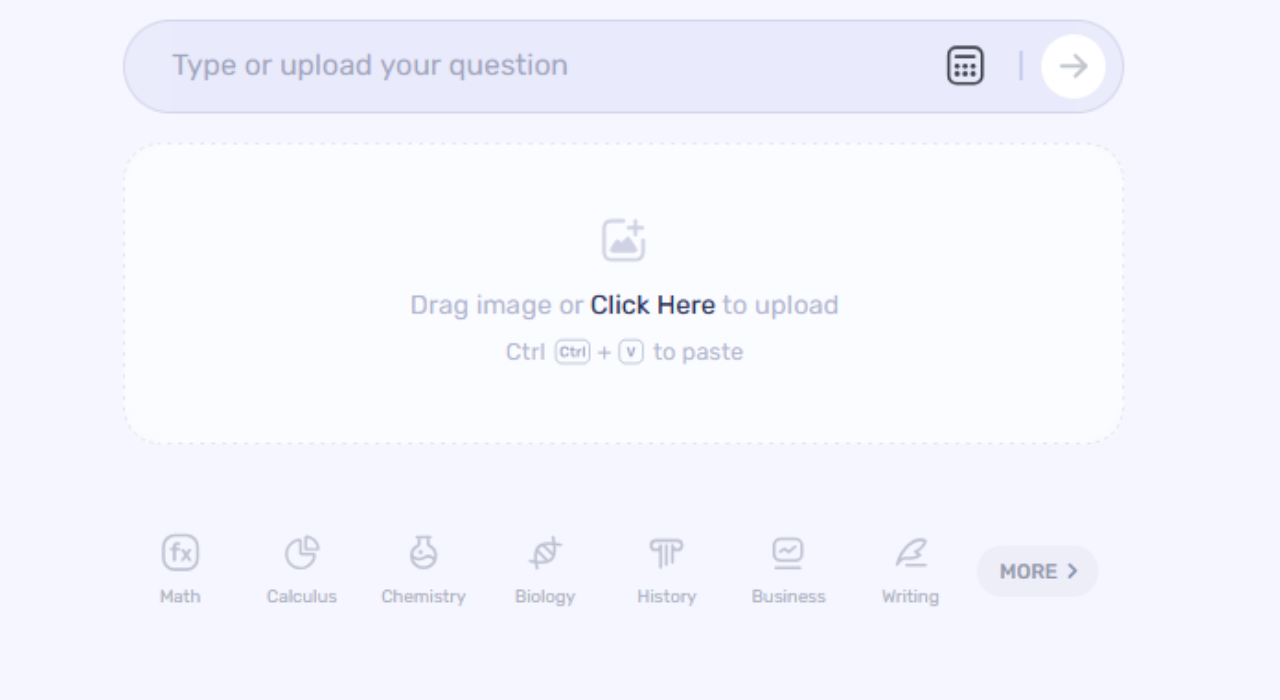
Step 1. Enter Query
The initial step is to enter your query or transfer an image of the issue you want assistance with. Gauth utilizes progressed calculations to investigate the data given and create an answer for the issue. You can type in the query you want assistance with or just snap an image of it and allow Gauth to wrap up.
Step 2. Get Results
Once you have entered your query or transferred an image, essentially press enter. Gauth will then handle the data and furnish you with a definite answer to the issue. This might incorporate bit-by-bit guidelines, clarifications, and, surprisingly, visual guides to assist you with better grasping the solution.
Step 3. Copy or Duplicate Data
After you have gotten the outcomes, you can decide to either duplicate the solution given by Gauth or recover it. In the event that you are happy with the solution and simply have to involve it as a reference, you can essentially duplicate it and save it for some time in the future. Notwithstanding, to investigate various ways of tackling the issue or check for elective solutions, you can decide to recover the outcomes and see various ways to deal with the issue.
To Conclude
To protect privacy amid rapid technological advancements, carry areas of strength for out, uphold information assurance regulations, and advance computerized education. Empower the utilization of protection-centred instruments, keep up with straightforwardness about information use, and routinely update security conventions. Drawing in partners in approach improvement guarantees thorough and versatile security assurance.